Tips to avoid being tricked by the common cyberattacks hitting schools and workplaces

Even before the pandemic, we were carrying out a huge portion of our day-to-day tasks and work lives online. And since then we’ve shifted even more to doing business within entirely digital environments. But for all the problems this hyperconnected world solves for us, it also means that cybercriminals have increasingly sophisticated means to exploit it. In the financial year, the equivalent of one cyberattack every eight minutes was reported to the Australian Cybersecurity Centre (ASCS).
When a cyberattack is successful, criminals gain illegal access to data stores on a computer or a network. In education environments, such information can be incredibly sensitive, and in the case of ransomware attacks can cost workplaces immense sums of money.
Two forms of cyberattack in particular are on the rise in Australia: phishing – which comes in the form of a disguised email or SMS – and ransomware, malicious software that blocks access to a organisation’s IT system or encrypts its data until a ransom is paid.
Phishing scams are growing exponentially – by 75% during the pandemic, while ransomware attacks rose 15% in 2020-2021. Overall, Australians reported loss of a total of $851 million dollars to scams in 2020 but the number is likely to be far higher.
Phishing: A threat you probably see daily
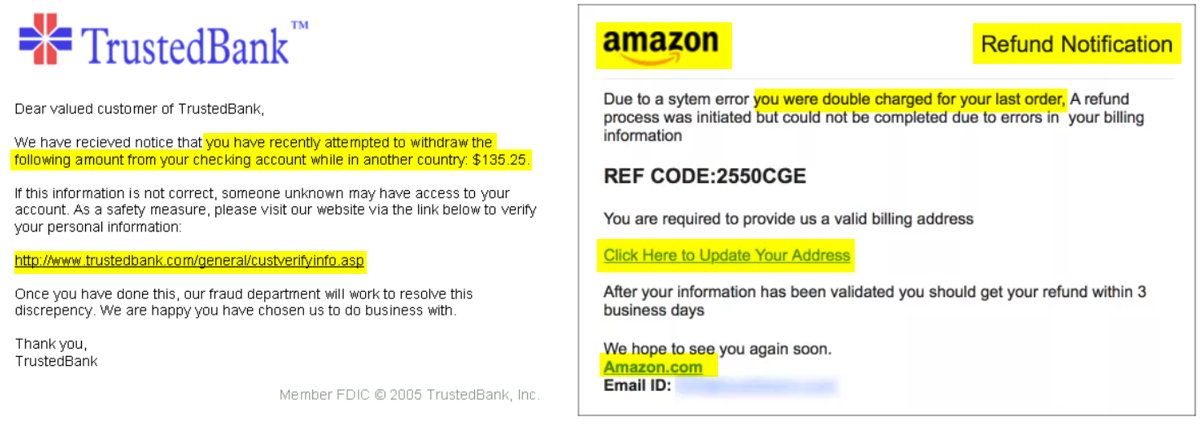
For us day-to-day email users, general phishing attacks have become all too familiar. In these attacks victims receive an email or text message that appears to have been sent by a legitimate institution and convinces the recipient into providing their sensitive data such as personally identifiable information, banking and credit card details, or passwords. Criminals then use this to access accounts and steal identities or money.
Phishing emails have a sense of urgency that criminals have carefully designed to override our common sense. It’s easy to go into work-mode and miss the warning signs. But given what is at stake, it’s wise to get into the habit of treating most unexpected emails as containing a potential threat.
Phishing emails are designed to appear to come from a legitimate source that are common to a lot of us, such as Amazon customer support, a bank, PayPal, your workplace’s software application providers, or other recognised organisation. Cybercriminals hide their presence within the sender’s URL, an email attachment link, and more.
The email will give the impression that you stand to lose something very valuable if you don’t click the link: ‘Someone’s tried to log in to your email’, ‘Your bank has suspended your account’, or ‘Someone just used your Apple ID to order a $500 device’.
Criminals have gotten a lot better at disguising these emails, so that when viewed in a hurry, it’s difficult to tell that they’re fake. The email will be accompanied by a seemingly identical logo to the organisation, as well as its fonts or a legitimate-looking footer.
Examples of requested actions in these emails include clicking an attachment, updating a password or responding to a social media connection request.
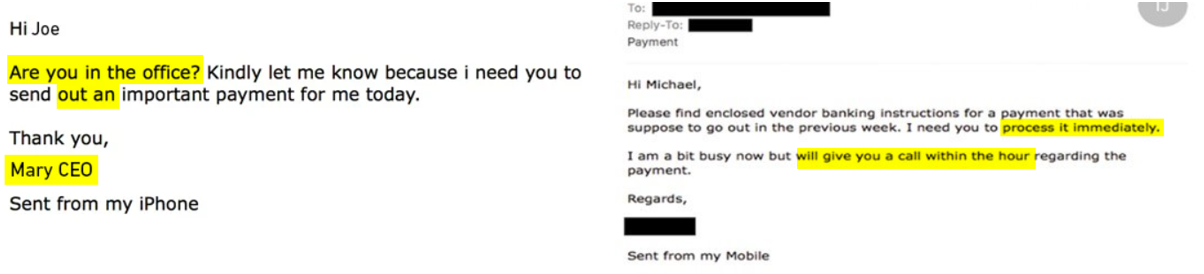
Spear phishing: An attack that calls you by name

Janison
Janison is a leading edtech provider transforming the way assessments are delivered and experienced worldwide.